Which of the Following Best Describes the Threat Modeling Process
Identifying the security objectives. Which of the following BEST describes an unknown penetration test.

Ip Value Chain In 2022 Chain Trade Secret Templates
Threat modeling is a structured process to identify and enumerate potential threats such as vulnerabilities or lack of defense mechanisms and prioritize security mitigations.

. The following subsections show the details about 41 approach and how this could help in the threat modeling process. This process of understanding and documenting security requirements is known as Threat Modeling and Security Analysis TMSA. Which threat modeling component identifies potential threat sources what these adversaries can do and how likely these attacks are.
Upon completion of the threat model security subject matter experts develop a detailed analysis of the identified threats. 1Fixed 2Iterative 3Seldom refined 4Deterministic. Threat Modeling Interview Question-Answer.
Analysis of actions taken. Identify your objective concisely. Applied to software it enables informed decision-making about application security risks.
When building an effective threat modeling process to identify specific risks and prioritize how you will handle them you need to consider the following steps. Which of the following best describes the type of penetration test Miguel is performing. The process of analyzing an organizations security and determining its security holes is known as.
Threat modeling is a process for capturing organizing and analyzing all of this information. Iterative best describes the threat modeling process Correct Answer is b Iterative. Analysis of actions taken.
Which of the following best describes the threat modeling process. Threat modeling is a structured process through which IT pros can identify potential security threats and vulnerabilities quantify the seriousness of each and prioritize techniques to mitigate. Describes the designs object model.
Mitigation steps for each threat. The Visual Agile and Simple Threat VAST Modeling method is based on ThreatModeler an automated threat-modeling platform. The process of identifying assets and threats in an organization is known as _____.
Which of the following security property does Spoofing violate. Threat intelligence asset identification mitigation capabilities risk assessment and threat mapping. A list of potential threats.
Q1 The following is a part of a threat model except _________. A high level description of the application. Validating that threats have been mitigated.
A typical threat modeling process includes five steps. Logical View Create a logical map of the Target of Evaluation. A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organizations financial assets.
Which of the following BEST describes the process by which code is developed tested and deployed in small batches. The process continues with identifying and prioritizing potential threats then documenting both the harmful events and what actions to take to resolve them. The version of the application examined.
Iterative best describes the threat modeling process Correct Answer is b Iterative. There are five major threat modeling steps. Which threat modeling measurement is used to describe how an attack can exploit a vulnerability.
To design-in security it is recommended that developers and manufacturers analyze the operating environment to determine how each device could be attacked and then document it. _____ generates a map that illustrates how the user moves through various features of the application. Which of the following security property does Spoofing violate.
Is performing a penetration test on a web server. Which of the following best describes the threat modeling process. In addition to producing a model typical threat modeling efforts also produce a prioritized list of security improvements to the concept requirements design.
A requirements model is the foundation of the _____ methodology. Information identifying the threat model typically includes the the following. Know your assetsdata not just physical.
Its scalability and usability allow it to be adopted in large organizations throughout the entire infrastructure to produce actionable and reliable results for different stakeholders. Threat modeling should be part of your routine development lifecycle enabling you to progressively refine your threat model and further reduce risk. Define general security objectives and scope.
Microsofts process of threat modeling can be utilized to do the process of threat risk modeling which performs below important tasks. Threat modeling consists of defining an enterprises assets identifying what function each application serves in the grand scheme and assembling a security profile for each application. The Process for Attack Simulation and Threat Analysis PASTA is a seven-step risk-centric methodology.
Ensure security is included in your business requirements. Miguel was given only the servers IP address and name. _____ generates a map that illustrates how the user moves through various features of the application.
Creating an application diagram. A requirements model is the foundation of the _____ methodology. 1Process Flow Diagram 2Sequence Diagram 3Data Flow Diagram 4Entity Diagram.
Threat modeling is a procedure for optimizing application system or business process security by identifying objectives and vulnerabilities and then defining countermeasures to prevent or mitigate the effects of threats to the system. Surveying or over-viewing of the application. The owner of the threat modeling document.
It is better to perform threat modeling from the early stages of the SDLC. Threat modeling intends to equip defenders and the security team with an analysis of what security controls are required based on the current information. This involves understanding how threats may impact systems classifying threats and applying the appropriate countermeasures.
Which of the following best describes the threat modeling process. Identifying threats and vulnerabilities. The name of the application examined.
The purpose is to provide a dynamic threat identification enumeration and scoring process.
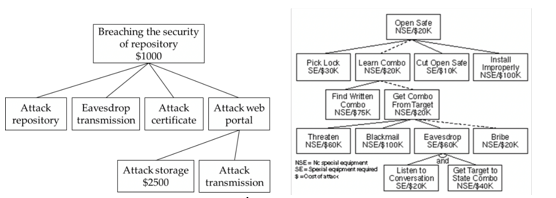
Threat Modeling 12 Available Methods

Threat Modeling 12 Available Methods

Arrow Process Diagram Template For Powerpoint And Keynote Process Infographic Diagram Design Powerpoint

Secure Devops For Aks Azure Solution Ideas Microsoft Docs Solutions Azure Security

Porter S Generic Strategies Porter S Generic Strategies Leadership Strategies Strategies

The Reliable Proxy Service For Best Secure Server Local Proxies Computer Security Cyber Security Best Computer

The Acculturation Model Identifies Group Factors That Are Likely To Create Social Distance Between Learner And Target Gr Learning Social Distance Culture Shock

U Vs M Form Organizational Structure Fourweekmba Organizational Structure Organizational Corporate Strategy

Putting The Ai Cart Before The Data Horse Dataops As Part Of A New Enterprise Stack Cloud Infrastructure Agile Software Development Wrike

Kaios Feature Phone Business Model And Why It Matters So Much Fourweekmba Vertical Integration Business Strategy Online Marketing Services
Threat Modeling 12 Available Methods

Wikimedia Commons Has Media Related To Diagrams Flow Chart Data Flow Diagram Decision Making

Threat Modeling 12 Available Methods

A Step By Step Roadmap That Describes The Synergy And Context Between Business And It Information Governance Operating Model Technology Roadmap

What Is The Aida Model And Why It Matters Fourweekmba Competitive Intelligence Strategies Blue Ocean Strategy

Tracing The Rainbow Through The Rain Learning To Ride The Emotional Waves Dialectical Behavior Therapy Dbt Skills Dbt

Organizational Silos Primer Https Flevy Com Browse Flevypro Doc 3842 Despite The Emergence Of Organizational Design Change Management Corporate Communication

Cybersecurity Reference Strategies Linkedin Cyber Security Enterprise Architecture Microsoft Ignite

Comments
Post a Comment